Our computers serve as portals to a host of services and information that we use every day in today’s hyper-connected world.
However, with the use of modern technology, hackers and other malicious individuals can remotely access and manage our computers without our knowledge or permission. This makes it very important to know how to check if someone is remotely accessing your computer.
I recently heard of an acquaintance who discovered that someone had been remotely accessing his computer without his knowledge for weeks. He noticed that his computer was running slower than normal and that various strange programs were running in the background.
These types of incidents are frequent, so it is essential to be alert to any indication that someone is spying on my computer remotely. This blog post will discuss how to tell if someone is remotely viewing your computer, as well as security and privacy precautions you can take.
Can remote access be traced?
Tracking remote access isn’t always easy, but it’s not impossible either. If you suspect someone is remotely accessing your computer, take steps to collect evidence, such as taking screenshots or recording behavior. You can also review your computer logs for any indication of remote access.
You can ask a computer security expert for help if you are unable to collect evidence on your own. They can give you advice on how to protect your computer and help you determine if someone is accessing it remotely.
How to check if someone is remotely accessing your computer?
These warning indicators point to possible remote access to the computer:
suspicious network activity
You may notice unusual network activity, such as increased network traffic or a slower Internet connection if someone is remotely accessing your computer. Also, unknown devices or unexpected links to your network may appear. If you notice any suspicious behavior, you should investigate it immediately.
Use Task Manager to detect remote access
It is the best method to monitor covert remote users. It is known as Task Manager on Windows computers and Activity Monitor on Mac computers.
Steps to use Task Manager in Windows to find remote access:
- Find one of the following options in Task Manager by selecting it from the taskbar menu.
- Then you can see the list of running applications on your computer.
- Any of the apps you haven’t run clearly indicates a remote viewer.
Strange mouse clicks or movements
It can be an indication that someone is remotely controlling your computer if you notice strange mouse movements or clicks. This is so someone else can operate your keyboard and mouse and use your computer without your knowledge. Remote access makes it possible.
Your webcam or microphone is active without your knowledge

It is obvious that someone is remotely accessing your computer if your webcam connected to your laptop is turned on without your knowledge. They may be watching you or listening to what you say. If you’re not using your webcam or microphone, cover them to maintain your privacy.
slow performance
It can indicate that someone is remotely accessing your computer if the computer is running slower than normal. This is due to the fact that remote access makes use of the capabilities of your computer, which can cause your system to lag.
Unauthorized access to your accounts
It may be a sign that someone is remotely accessing your computer if you notice unauthorized access to your accounts, including email, social media, and banking. This is due to the possibility that remote access allows someone to access your login information and log into your accounts without your knowledge.
How to know if your Mac has been accessed remotely?
Mac computers are known for their security features, but they are not immune to remote access. Here are some signs that your Mac might have been accessed remotely:
Strange messages or popups
Strange pop-ups or messages on your Mac can indicate that someone is remotely accessing your computer if you detect them. These pop-ups or messages can be used to track your online behavior, steal sensitive data, or take control of your machine.
Unknown files or programs
Someone may have uploaded unknown programs or files remotely if they find unknown files or programs on your Mac. These applications or files can be used to monitor your online behavior, steal sensitive data, or take control of your machine.
Changes to your system preferences
Someone may have accessed your Mac online if the system preferences on your Mac have changed. It is essential to check for unapproved changes because remote access can be used to change your system settings without your knowledge.
How to prevent someone from accessing my computer remotely?
If you want to prevent remote access to your computer, here are some steps you can take:
disconnect from the internet
Disconnect from the Internet immediately if you think someone is accessing your computer directly. As a result, the remote user will not be able to access your computer, giving you time to protect it.
block remote desktop
Windows has a feature called Remote Desktop that allows remote access to your computer. Disable remote access if you don’t require it to prevent unauthorized users from accessing your computer.
Use a firewall
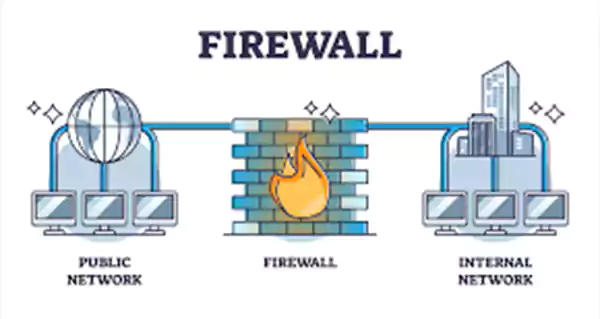
By blocking incoming connections, a firewall can help protect your machine from unauthorized entry. Make sure your firewall is properly configured and enabled.
Configure the antivirus program

Your computer can be protected against malware that can be used to gain remote access by using antivirus software. Make sure your antivirus software is up to date and loaded.
Use strong passwords
For all your accounts, use strong passwords and update them frequently. This will make it more difficult for someone to reach your computer remotely.
Enable two-factor authentication
Your accounts become more secure by using two-factor authentication. Even if someone already has your login information, this will stop unauthorized access to your accounts.
final thoughts
We have covered many indicators to indicate that someone is remotely accessing your computer in this blog. If you think someone is spying on your phone or remotely accessing your computer, you need to be vigilant and move immediately.
We hope that you are now fully aware of how to tell if someone is remotely viewing your computer and how to protect yourself against such dangers.
Fountain:
Co-authored with Yaffet Meshesha and Nicole Levine, MFA: https://www.wikihow.com/Detect-a-Remote-Access-to-My-Computer
Read More Author: Prakhar Shivhare I am a Bachelor of Commerce (Hons) graduate of Hansraj College (University of Delhi) with demonstrated knowledge and skills in domains of writing, health, fitness, internet and research.
Categories: How to
Source: vtt.edu.vn